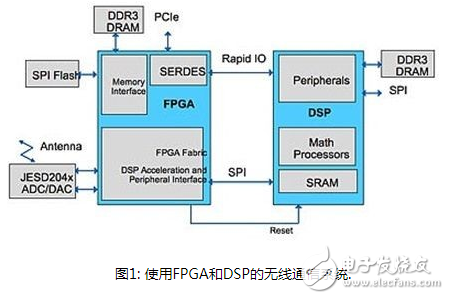
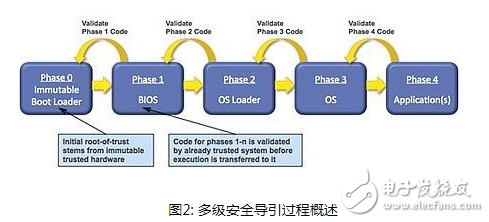
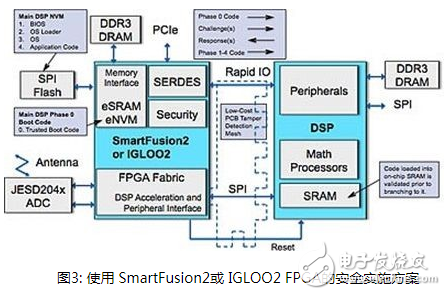
For digital signal processor (DSP)-based designs, if the DSP does not have sufficient security capabilities, it is particularly vulnerable to intrusion. In many applications, if you use FPGA as a cooperation to offload part of the work of the DSP, you can easily implement advanced security functions. Moreover, if the matched FPGA uses flash storage technology to store the configuration bit stream and key key information in the structure on the chip, it can achieve inherent security against copying or cloning, allowing designers to automatically protect the design from these Types of theft. DSP and FPGA system structure In a system using FPGA or DSP (Figure 1), the DSP implements advanced signal processing algorithms, and the FPGA implements the front-end extraction function. The high-speed serial RapidIO bus is used to connect FPGA and DSP; FPGA is also connected to PCIe bus and used as a remote access management port via the Internet. The PCIe bus can also bridge the traffic entering and leaving the RapidIO bus to connect extended remote management to the DSP. The FPGA controls an external DDR3 DRAM, which is used as a buffer for the data packets sent and received by the wireless interface, and allows the FPGA to offload any low-level data protocol processing and buffer management functions from the DSP. The FPGA will also be responsible for "guiding" the DSP from the external SPI Flash. The FPGA uses its own SPI memory as the source of the DSP code, and maps the boot process through the guidance function of the SPI port from the DSP. Once the code transfer is complete, the FPGA allows the DSP to begin execution. Security root If the system does not protect the guidance process, the intruder can replace it with his own code and then effectively hijack the entire system, which may lead to system damage, major financial losses, and possible personal liability. We must use a secure guidance process to minimize such attacks, and the hardware root of trust is a necessary condition for implementing a secure guidance process. The hardware root of trust supports the verification of system data integrity and confidentiality, and can extend this trust to internal and external entities. The hardware root of trust can avoid intrusion or modification, and can also be used as a starting point for laying more advanced functions safely. In an embedded system, the root of trust works with other system components to ensure that the main processor uses only authorized codes for safe guidance, thereby extending the trust zone to the processor and its applications. The hardware root of trust must be built on a secure FPGA, and its configuration bit stream must be protected from copying or reverse engineering to avoid damage to the root of trust by malicious intruders. Therefore, protecting the intellectual property (IP) of FPGA devices is a necessary condition for protecting the rest of the embedded system. Safety requirements for multi-level guidance process The initialization of the embedded processing system from other parts requires a safe guidance process to execute trusted code that is not affected by malicious content or leaks. Figure 2 shows the different stages that the security guidance process must go through in order to fully protect the initialization of the embedded system. Each stage must be verified by the previous successful stage to ensure the "chain-of-trust" up to the top application layer. The unmodifiable bootloader (stage 0) code can be embedded in the FPGA device, and verified through a secure root of trust, using a protected security key and related security algorithms to ensure the integrity and authenticity of the code. Before the code and execution are transferred to the sequence phases of each security guide, these phases must be verified by a previously trusted system. Implement a secure embedded system Encrypted bitstream data is a common method to protect the configuration bitstream used for power-up (just like the SRAM-based FPGA configuration bitstream). This makes it more difficult to capture the bitstream only by observation during configuration startup. The decryption key is stored in the FPGA and is used to decrypt data before configuring the FPGA. It is usually necessary to use a battery in order to retain the security key in the event of a power failure. Another way to protect the FPGA configuration bit stream is to use non-volatile memory to store it completely on-chip to avoid exposure during startup. Some FPGA devices, such as Microsemi's SmartFusion2 and IGLOO2 series, also provide additional protection by encrypting the bitstream during programming during manufacturing. This also protects the design from copying or reverse engineering by unethical contract manufacturers, causing the required hardware root of trust to be destroyed. Once we have created a secure FPGA, the next major requirement is to implement a hardware root of trust. FPGA must protect the security key and the unalterable initial phase (Phase 0) bootloader on the chip so that malicious intruders cannot attack or modify them at all. If you use a Flash-based FPGA to store immutable codes and security keys on the chip, you can also load the configuration bit stream through the configuration process to gain security. The security key is only a small part of the overall design, however, it is very important to protect the design from other forms of attacks. Stop the attack A common attack method is to use side-channel analysis (such as observing the power or timing signature during the operation of the security key) to try to find out the security information on the chip. This side-channel method is similar to the method in which a safe thief constantly manipulates the lock and listens to the noise of the movement to find a safe combination. In this case, the side channel is the sound caused by the physical implementation of the safety "function". The implementation of a decryption algorithm designed to withstand channel attacks can withstand more advanced side channel attacks in the form of differential power analysis (DPA). If DPA-resistant technology is not used, observers can measure the power used by the design in processing keys and algorithms. In addition, frequent changes to the security key will limit the number of measurements used by attackers for data analysis, making it difficult for them to use this type of method to invade. Moreover, circuit design techniques such as pre-charge registers and buses will limit the "noise" that intruders can use. Comprehensive overview Now that the security of the FPGA IP has been protected, and our design has established a root of trust, we can examine the entire embedded system implementation in more detail. Figure 3 shows an implementation of a secure embedded system, which describes the different components of the secure guidance process. The immutable boot code and key are stored on the chip, and the external SPI memory stores the remaining DSP code (including any required OS loader and OS code, as well as application code), all of which use the security challenge of the root of trust management And response system to verify. At the end of the process, the secure code is loaded into the SRAM on the DSP chip, and the FPGA allows the DSP to operate, making sure that only the authorized code is executed. In addition, using FPGA I/O can easily implement low-cost PCB tampering detection solutions to detect any attempts to drill or cut traces and implement protective measures. Once the security guidance is completed, the FPGA can implement other functions required by the system, such as bridging PCIe and RapidIO interfaces, connecting to the JESD204x bus, preprocessing wireless signals through the FPGA module, and controlling the DDR3 cache. When additional algorithm processing power is required, SmartFusion2 has an on-chip processor to choose from; when the FPGA module is sufficient to implement the required control functions, IGLOO2 can also be selected. Securing the new DSP design for the Internet of Things Flash-based FPGAs provide security IP and hardware root of trust, which are used to build higher-level security functions, such as security guidance, to protect the design from intrusion. Future security requirements will be based on these functions. For example, transmitting secure data and authorizing security devices will become the main requirements for emerging IoT and M2M applications, which will target many new DSP-related designs. This will require several additional design security layers to protect the embedded system design IP. In addition, new data security requirements are expected to grow significantly, and advanced security technologies and methods are needed to fully meet the requirements for lower power, smaller footprint, and higher processing efficiency in order to succeed in these new markets. Tr90 Glasses,Tr90 Perspective Glasses,Tr90 Sunglasses,Tr90 Material Glasses Danyang Hengshi Optical Glasses Co., Ltd. , https://www.hengshi-optical.com