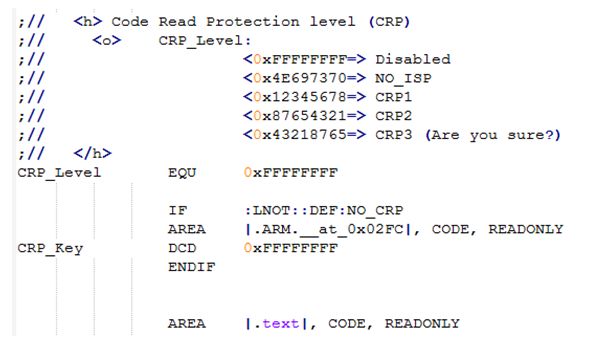
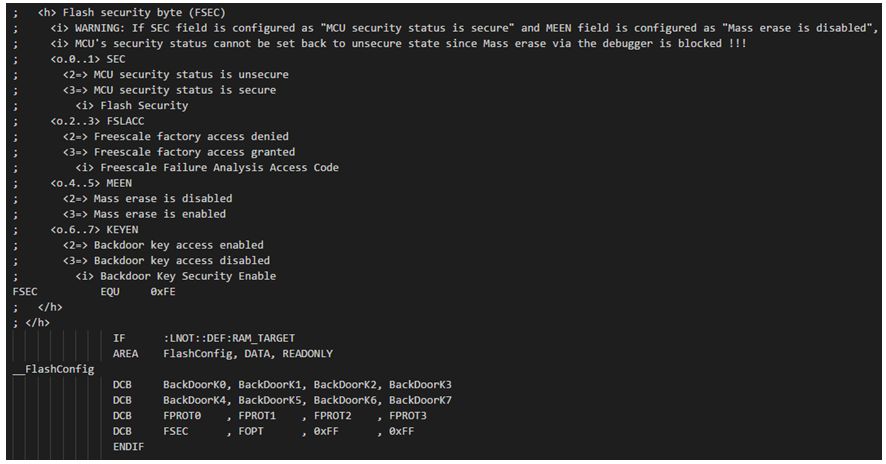
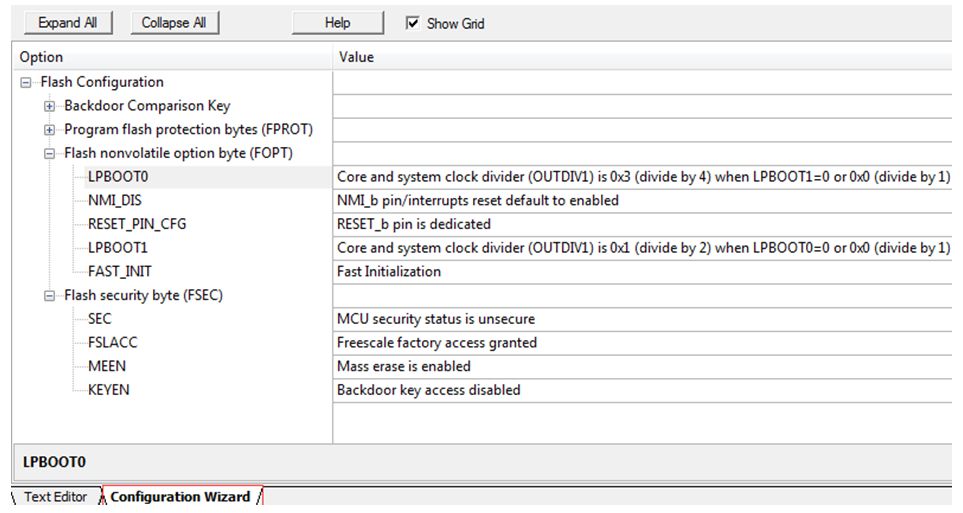
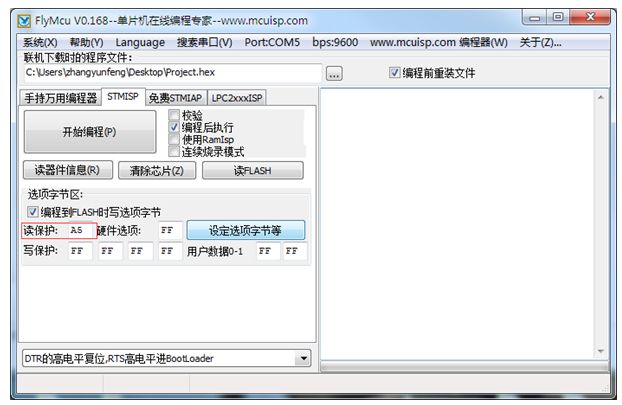
With the emergence of the Internet of Things and edge computing, a variety of MCUs are also used. How to ensure that our program security and intellectual property rights are not violated? In this article, we will explain the program encryption of mainstream MCUs, and hope to help you choose the most suitable Microprocessor for own application. 1. MCU encryption The usually mentioned MCU encryption refers to protecting the user's program firmware to prevent others from reading the program written in Flash through an external debugging interface or other methods. Protect your own plan from being copied easily by others, and protect your own intellectual property from the hardware. MCU encryption also refers to preventing one's own program from being read and cracked maliciously. 2. Commonly used MCU encryption methods By writing specific configuration words; Increase external encryption chip; Encrypt the program code with a password, so that the program becomes ciphertext; The program verifies the unique ID of the chip. 2.1 Configuration word encryption 2.1.1 Principle MCU manufacturers add specific non-volatile storage to the chip when designing the chip, and this storage may also be a specific address area of ​​Flash. The user can write the value to enable storage protection through an external tool or at a specific address in the program. Configuration word encryption will take effect after the chip completes the power-on sequence, and generally includes the following functions: Disable debugging interface (JTAG/SWD); Can not help debugging interface, but not allow debugger to connect to the kernel and access Flash and RAM space; Close the ISP command for reading and writing Flash; It is forbidden to read Flash operations except for the chip's normal execution of programs; Disable the chip to start executing code from the external interface or RAM. 2.1.2 Application scenarios This encryption method is usually used in systems where the program is stored in the internal Flash of the chip. For example, NXP LPC series MCU, GD32 series MCU, NXP Kineits Cortex-M series. 2.2 External encryption chip 2.2.1 Principle The way the encryption chip protects the program is to confirm whether the program is further executed through the interaction between the program and the external encryption IC. Using chip random number peripherals or other mechanisms that can generate random numbers, the system obtains a random number after each power-on, and transmits this random number to an external hardware encryption IC through an IIC-like protocol. The system then calculates the result according to the previously agreed algorithm, and waits for the external IC to receive the random number and calculate the result. The external IC will send the calculation result back to the system. If the calculation result of the system and the calculation result of the external IC are the same, it means that the external encryption IC exists. 2.2.2 Application scenarios This encryption method is mainly used by users to encrypt key algorithms in the code. The algorithm is usually provided in Lib. Only customers who have purchased the corresponding encryption chip (similar to the product key) can use the algorithm program. 2.3 UID verification encryption 2.3.1 Principle UID encryption is a way that users actively encrypt. At present, almost all processors contain UID internally, which can be obtained by direct address reading or IAP instructions. UID encryption is usually divided into two ways: When programming the program, the user reads the chip UID once and writes it into a specific area of ​​Flash. When the program is started, directly read the UID and the value in the Flash to compare to determine whether to start; After the user reads the UID, the UID encrypted information is written to the Flash specific address, such as the last sector of the Flash, through the private key. When the program is started, the chip UID is first read and calculated through the same key and algorithm, and then compared with the value in Flash to determine whether to start. The first type is the easiest to crack, and the second type also has potential risks. In order to enhance the security of the second type, the encrypted data can be split and stored in different locations in the Flash, and then combined during runtime. 2.3.2 Application scenarios Mainly used in some protocol stacks that do not require much protection, such as LoRa protocol stack, file system, private operating system, etc. The value of the protocol stack relative to the algorithm will be lower, and the cost of adding an encryption chip is too high. At the same time, this method can also be extended to use PID (the ID of each model is the same) to distinguish device models. 2.4 Program firmware encryption 2.4.1 Principle Program firmware encryption means that the entire program firmware is encrypted and calculated with a private key to generate ciphertext, so that the program cannot be decompiled even if it is obtained by others. This kind of encryption usually requires a section of address storage key and decryption program, which can be the internal Bootloader of the chip or the user's own Bootloader. 2.4.2 Application scenarios This encryption method is mainly used for products where the chip has no internal Flash or the Flash is small, and the user needs to upgrade the firmware. E.g: When the chip starts from the external Flash, the external Flash is easily copied and pirated. This kind of application usually has an OTP area inside the chip for programming keys; When the internal Flash of the chip is small, the algorithm and other files can be placed in the external Flash and decrypted to the internal RAM for execution during operation. The key is usually stored with the internal Flash program; Used in projects where the product needs to be upgraded later, the decryption program can be placed in the Bootloader. During the upgrade process, the Bootloader decrypts the received firmware and writes it to the internal Flash. In this way, you can send products to update the firmware at will without worrying about intellectual property infringement. For example, the i.MX RT1050 series chip is encrypted by the program firmware. The program is placed in the external Flash and executed while decrypting. For the encryption of the i.MX RT1050 series, please contact us. 3. Encryption methods of commonly used chips 3.1 NXP LPC series Most LPC series MCUs use configuration word encryption, namely CRP (Code Read Protection) encryption. Write the configuration word (CRP Key) to a specific Flash address. After the chip is powered on, the internal boot will disable the corresponding function according to the configuration selection. CRP is a mechanism that allows users to enable different levels of security in the system, thereby restricting access to on-chip flash memory and the use of ISP. When needed, call CRP by programming a specific pattern in the flash memory location at 0x0002FC. IAP commands are not affected by code read protection. Take LPC824 as an example, find the CRP Key in the startup file (*.s) and modify it as needed, as shown in Figure 3.1. Figure 3.1 CRP Key example Note: Remember that CRP3 can only be used in the final product firmware, otherwise the chip will be locked and cannot be unlocked. 3.2 NXP Kineits Cortex-M series The encryption of the Kineits Cortex-M series also uses configuration words to write to specific areas of Flash, but it is more complex and more powerful than the LPC series. The encryption of the Kineits Cortex-M series is contained in the FlashConfig area. FlashConfig contains some configuration information for the internal Boot of the chip, such as enabling or disabling the NMI pin interrupt. Figure 3.2 FlashConfig section of FSL You can use the keil tool to quickly use the UI configuration, as shown in Figure 3.3: Figure 3.3 Start file configuration 3.3 GD32 series GD32 series encryption is similar to STM32 series encryption. GD32 contains an FMC peripheral. FMC provides a safety protection function to prevent illegal reading of flash memory. This function can well protect software and firmware from illegal user operations. FMC contains an OB_RDPT byte and its complement byte: When the OB_RDPT byte and its complement byte are set to 0x5AA5, after the system is reset, the flash memory will be in a non-safety protection state; When setting the OB_RDPT byte and its complement byte value to any value other than 0x5AA5, after the system is reset, the security protection status will take effect; In the security protection state, the main storage flash memory block can only be accessed by user code and the first 4KB flash memory is automatically in the page erase/program protection state. In debug mode, or when booting from SRAM, and when booting from the boot loader area, the operation of the main memory block in these modes is prohibited; If the OB_RDPT byte and its complement byte are set to 0x5AA5, the security protection function will be invalid, and an entire chip erase operation will be triggered automatically. GD officially provides encryption tools GigaDevice_MCU_ISP_Programmer or use FlyMCU and other tools. The operation interface is shown in Figure 3.4: Figure 3.4 GD32 uses FlyMCU encryption 3.4 i.MX RT series The i.MX RT series is a cross-border processor released by NXP, the processing performance of MPU, and the development method of MCU. This series does not include internal Flash available to users, and all codes must be stored in external storage media. It uses FSL's unique HAB security mechanism, which can achieve a more secure encryption mechanism than before. The encryption of i.MX RT is to completely convert the program firmware into cipher text by tools, and cannot be decompiled. At the same time, i.MX RT contains an OTP area for programming key information and startup information, which cannot be read after encryption. When the chip uses QSPI or HypeFlash, it can be decrypted while running without occupying additional RAM space. At the same time, hardware decryption with the 32KB ICache and 32KB DCache in the kernel makes the program running will not be affected by firmware encryption; The chip also supports full decryption of the program to internal RAM or external SDRAM when Booting. The startup speed of the code in this way is slightly slower, but it can support more startup methods: SD card, MMC, Nand Flash, etc. NXP provides encryption tool CSF and key burning tool FlashLoader for encrypting and burning program firmware. If you have any questions, please contact our FAE for support.
RCA Cables can be used to connect a variety of audio and video devices, such as camcorders, to TVs or stereos to speakers. Most high-end camcorders have all three RCA jacks, so the signal entering or leaving the device goes through three separate channels-one video and two audio-resulting in a high-quality transfer. Lower-end camcorders usually have only one jack, called a stereo jack, which combines all three channels. This results in lower-quality transfers because the signal is compressed. In either case, RCA cables transmit analog, or non-digital, signals. Because of this, they cannot be plugged directly into a computer or other digital device. RCA cables connect amplifiers to all sorts of devices.
Ucoax OEM Cable Assembly RCA Cables
Quality of RCA Cables
Several factors affect the quality, price, and performance of RCA cables:
Materials: The connectors on RCA cables are often gold, silver, or copper. As you might expect, the gold connectors are the most expensive. They're also better than silver and copper connectors at preventing oxidation, but not as good at electrical conductivity. The silver connectors are best for electrical conductivity with the copper cables coming in a close second and the gold cables falling far behind. Other suitable materials are nickel, zinc, and tin.
Cable Length: Cable length has a negative effect on signal quality. Buy a cable that is only as long as you need it to make the connection for the best signal quality.
Shielding: A well-shielded cable delivers a better signal than one that lacks robust shielding.
The other end of the cable: If possible, match the material used in the other end of the cable to the material used in the connectors. Don't match tin with gold or silver with gold. Those combinations can cause problems because of an electrolytic reaction.
High Quality RCA Cables, Male to Male RCA Cable, RCA Cables for HDTV UCOAX , https://www.ucoax.com