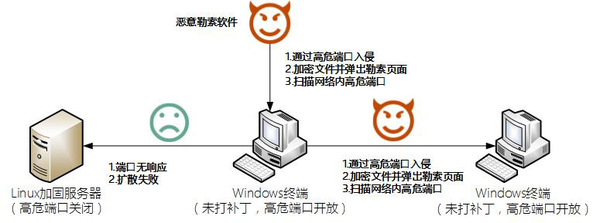
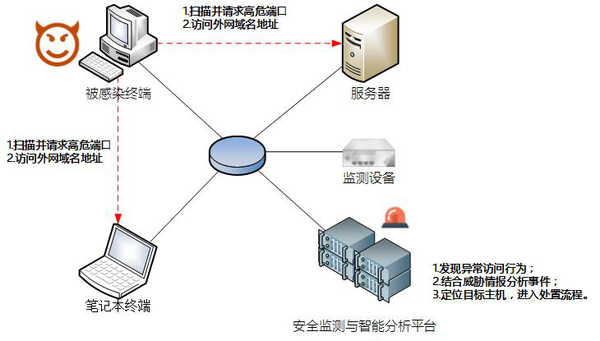
(Original title: Security Visualization, let WannaCry ransom the virus nothing) WannaCry? Ransomware attacked the virus quickly and spread all over the world. After the exploiters exploited the vulnerabilities to invade the Windows system, the encrypted files further extorted Bitcoin and the educational institutions, energy companies and government agencies suffered serious damage. The time of outbreak infection coincided with the weekend, and many security practitioners worked hard to work overtime and tried their best to reduce losses for users. We cannot help but think about how security managers should minimize losses after the virus has breached the borders. Xiao Bing interviewed Mr. Li Zhipeng, the technical director of Beijing Tianhang Wangan Information Technology Co., Ltd., and Li Zhipeng analyzed the characteristics of the virus in detail. The extension process provides some suggestions for defending against such attacks. How does the virus spread on the internal network? The larger the internal private network is, the more vulnerable it is to network virus intrusion, and the faster the virus spreads. This is a feature of the WannaCry worm incident this time. WannaCry? uses the Windows system to actively spread in portholes such as 445 and 139. Why do security devices such as vulnerability scanning and intrusion prevention deployed in internal networks not play their due role? Let’s re-combine the proliferation process after the virus enters the intranet, and see what we can do to reduce the loss during the virus proliferation process. To the lowest. First, the Wannacry virus spread using NSA Eternal Blue. Microsoft issued a patch in March but did not claim that the patch is related to a specific vulnerability. Hysteresis has not been found in the loopholes. In addition to the large number of terminals on the intranet, the delay in the patch distribution system has led to failure to do early defense work. Second, the virus lacks effective safety monitoring, situational awareness, and warning methods in the diffusion process. Even after discovering that a large range of terminals are locked by ransomware, they realize that the incident is serious. Although notifications and disposal measures are immediately issued, the virus has spread widely. Losses have already been caused. Managers can only interrupt the Internet in a large area and the impact on normal work is self-evident. How to proactively monitor and detect similar attacks in advance? Li Zhipeng mentioned that the affected educational institutions, large-scale energy companies, and certain government agencies have the same features. They use and maintain a large-scale internal network, with a large number of terminals and complex application systems. Due to the long construction period, it is difficult for administrators to grasp the details of all application systems, servers, and terminals in the entire network, and there is a lack of perspectives to monitor the real-time network behavior and application relationship of the entire network, which in turn leads to delays in response measures. What exactly is happening on the Internet? How is it affected? There is no visual means to sense the situation. Security managers are in a dangerous state where blind people ride horses and enter the dark pool at night. If the user can monitor the access relationship between terminals and applications on the entire network, the number of high-risk ports on the network such as the 445 will increase during the outbreak of the virus; the KillSwitch of the early virus will access a non-existent Internet domain name to judge Whether to continue the attack behavior, when a large number of terminals on the network access the same domain name at the same time, these behaviors are completely inconsistent with the characteristics of daily access behavior in the network. The system immediately generates an alarm; the user can also combine threat intelligence and security alarm events for follow-up. The basis for the safe disposal is as follows: After the occurrence of this security incident, major security vendors have provided disposal advice and tools. The implementation of security management system can effectively reduce losses. In the end, Li Zhipeng mentioned that although WannaCry?'s loopholes are more lethal, the means of communication are simple and even crude. In fact, they are easily monitored, but they still cause quite a lot of damage. Now that we have seen a clear trend, there may be a virus that exploits more lethal loopholes and adopts more covert means of transmission. To this end, we need to take proactive measures as soon as possible, assume monitoring and arming under the premise of having been invaded, perceive security posture through means such as security visualization, know ourselves, and establish proactive security management and technical support systems. (Original title: Security Visualization, let WannaCry ransom the virus nothing) Usb Wireless Charger,Best Wireless Charger,Wireless Charger Price,Wireless Mobile Charger wzc , https://www.dg-wzc.com