(2) Wireless sensor network Wireless sensor network is a brand-new information acquisition platform that can monitor and collect information of various monitoring objects in the network distribution area in real time, and send the information to the gateway node to achieve the specified range Target detection and tracking has the characteristics of rapid deployment and strong invulnerability. The regional home intelligent anti-theft alarm system uses the principle of wireless sensor network to deploy a wireless intelligent anti-theft alarm network, in which the wireless anti-theft alarm probe is a node in the cluster, the home host is the cluster head node, and the community host is the gateway node. The alarm information of the wireless anti-theft alarm probe can be gathered to the host of the community in time, and the host of the community can reflect it in time, so that the security personnel can respond quickly. The structure of the wireless sensor network is shown in Figure 3.
Multi-core cpu is more and more popular, people are used to take dual core processors laptop before. However, Quad Core Laptop is becoming selling like a hot cake nowadays. You can find Quad Core Processor Laptop at our store, like I3 Quad Core Laptop,I7 Quad Core Laptop, I5 Quad Core Laptop, intel celeron J4125 or N5095 15.6 Inch Laptop, even N4120 quad core 14 Inch Laptop, etc. Therefore, you can just share the parameters prefer, like size, cpu, ram, rom, gpu, application scenarios, thus save much time to get a win-win solution.
Do you know the reason why more people choose quad core device? The core reason is that heavier tasks people need to finish at a higher speed than before. Nowadays quick rhythm is becoming the main style in city even everyone is eager to downshifting. So more powerful laptop, computer, mobile phone is a trend, though most functions never are used in lifetime.
Other 15.6 inch Gaming Laptop or 14 Inch Gaming Laptop is becoming the most popular level at the market.
Quad Core Laptop,I3 Quad Core Laptop,I7 Quad Core Laptop,I5 Quad Core Laptop,Quad Core Processor Laptop Henan Shuyi Electronics Co., Ltd. , https://www.shuyioemminipc.com
This system uses a single-chip microcomputer control technology, wireless sensor network technology and GSM mobile communication technology to implement an intelligent anti-theft system with networking capabilities. The system adopts GSM mobile communication technology, which can enable the community security personnel and users to receive the alarm information in time and rush to the scene as soon as possible, thereby minimizing user losses. Using wireless data transmission, you can easily network. The alarm network can be large or small, from family use to community use, community networking, to regional networking. Using wireless data transmission, no need to re-wire, you can place monitoring probes at will, which is very suitable for residential and family use.
1 Working principle of intelligent anti-theft alarm system The intelligent anti-theft alarm system is mainly composed of 4 parts: wireless anti-theft alarm probe, home host, community host, regional host.
The wireless anti-theft alarm probe is generally installed on the window of the user's house. Its small and beautiful appearance can be directly attached to the window. The anti-theft alarm probe confirms the intrusion of thieves through the dual detection principle of vibration and infrared heat source. When the alarm situation is found, it immediately starts its own sound and light alarm to deter the intruders, and at the same time transmits the alarm information to the home alarm host through wireless data transmission. The home alarm host immediately sends the alarm information to the user's mobile phone, cell or area alarm host via SMS, and can also activate a high-power indoor sound and light alarm device to prevent further violations.
(1) Wireless anti-theft alarm probe The dual monitoring principle of vibration sensor and infrared pyroelectric sensor is used to confirm the existence of thieves and ensure the accuracy of the alarm. The probe adopts low power consumption design technology, low power consumption, and can work for more than one year using button battery power supply. Each wireless anti-theft alarm probe has a unique ID number, which can be matched with the actual location where it is installed. These location settings can be modified at any time through the user host, and the user can receive the precise location of the alarm (specifically the window location of the user's house) through the alarm message, which is convenient for notifying relevant personnel to arrive at the accident site as soon as possible.
(2) The home host can send an alarm message, and start the sound and light alarm in the living room. High-power electromagnetic relays are reserved to drive other home appliances for alarm and other actions. Alarm objects can be managed in groups (family, friends, security, etc.), so as to notify the nearest personnel to arrive at the scene of the accident as soon as possible according to priority, and reduce user losses.
(3) Community host and regional host Mainly identify the location of the alarm based on the content of the alarm message. Query the geographic information recognition system based on the contents of the alarm message and dispatch the nearest security personnel to the scene as soon as possible. The community host and regional host have user registration management functions, manage the user network user group in their jurisdiction, and manage the alarm log through the database system.
2 Intelligent anti-theft alarm system design plan
2.1 Wireless anti-theft alarm probe design scheme The wireless anti-theft alarm probe is installed on each window of the room. It has a small size and low power consumption. It can be directly attached to the window. When a thief is found, it can independently alarm with sound and light and send a wireless alarm Signal to home host. The hardware structure is shown in Figure 1. 
(1) Low power consumption design The wireless anti-theft alarm probe is powered by a button battery and requires a low power consumption processor. This scheme selects ATIny44 processor of Atreel Company. ATTIny is Atmel's low-power series products. ATtiny44 has three individually selectable low-power sleep modes, which makes ATtiny44 perform well on battery-powered devices. The application software can adjust the system clock frequency when needed to achieve the best power consumption performance, such as slowing down the clock frequency of some microprocessor modules when the system is idle. Using the AVR Power Stop System, users can turn off energy consumption modules such as timers and ADCs when they stop using the microprocessor. ATtiny44 consumes less than 10O nA in PowerDown mode. The size of the wireless sensor is required to be as small as possible for installation, and the small package of ATti-ny44 also makes the entire wireless sensor significantly smaller. ATtiny44 usually works in the power-down state, it is the minimum power consumption mode. When there is an alarm signal, the processor wakes up from the interruption to determine whether it is a thief intrusion, if not, it returns to the power-down mode, and if it is a thief intrusion, it starts the wireless transmission module to transmit wireless alarm information.
(2) Infrared pyroelectric sensors In nature, any object above absolute temperature (-273 K) will produce an infrared spectrum. The infrared wavelengths released by objects of different temperatures are different. Infrared wavelengths are related to temperature and radiation The amount of energy is related to the surface temperature of the object. The human body has a constant body temperature, generally around 37 ° C, and emits infrared rays with a specific wavelength of about 10 mm. The passive infrared probe works by detecting the infrared rays emitted by the human body. The sensor of the passive infrared probe contains 2 pyroelectric elements connected in series, and the directions of the two polarized electrodes are opposite. The environmental background radiation has almost the same effect on the two pyroelectric elements, causing their pyroelectric effects to cancel each other. The detector has no signal output. Infrared rays are strengthened by Fresnel filters and then concentrated to pyroelectric elements. When this element receives changes in human body infrared radiation, it loses charge balance and releases charges outwards. After detection and processing, it can generate an alarm signal.
(3) Wireless transmitter module The wireless transmitter module of the wireless sensor selects the CCll50 single-chip chip of Chipcon Company. CCll50 has abundant frequency resources and requires few external components. CCll50 has a sleep state, when there is no alarm information, it can be set to sleep state to reduce battery power consumption. When there is an alarm message, the wireless transmission module is woken up, and the wireless transmission module is turned off after the completion of the transmission of the alarm signal.
2.2 Home host design plan The home host is the core of the entire family's intelligent anti-theft alarm system. It can independently alarm after receiving the alarm signal to drive away the thieves, and can also send an alarm message to the community host and regional host to notify security. The personnel will arrive as soon as possible. The hardware structure of the home host is shown in Figure 2. 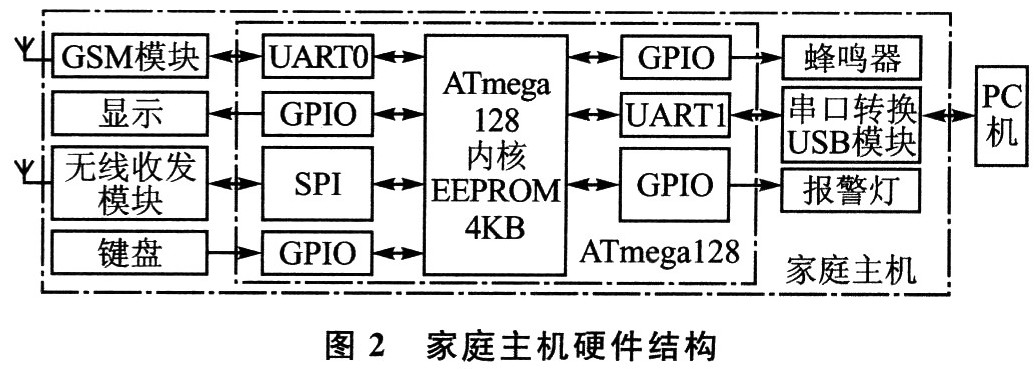
(1) Wireless transceiver module The home host uses Chipcon's CCllOO wireless transceiver chip, which can be matched with the CCll50 single-issue chip. It has rich frequency resources and high receiving sensitivity, which can fully meet the indoor wireless sensor signal receiving task. After receiving the wireless alarm signal, CCll00 transmits the received data to the single-chip microcomputer, the single-chip microcomputer analyzes the data, and then sends out audible and visual alarms and SMS alarm messages. 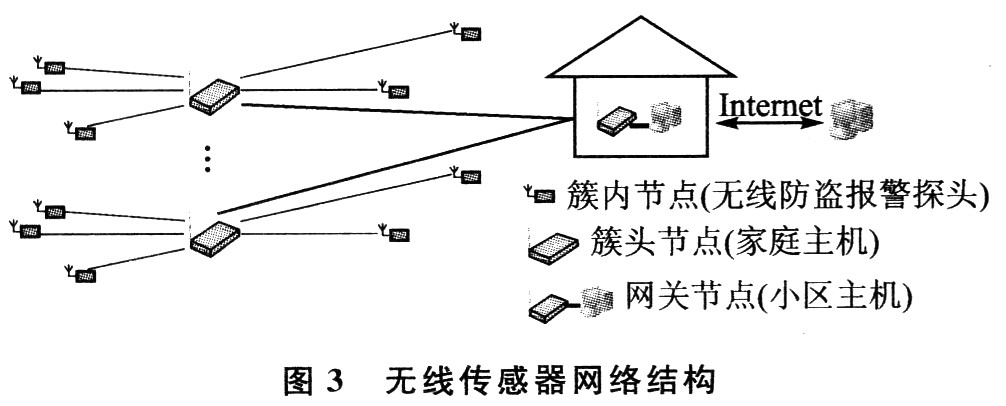
(3) Microprocessor The host computer has slightly higher requirements for the microprocessor. The microprocessor is connected to the wireless transceiver module and the GSM module at the same time, and has a host computer communication interface. This scheme selects ATmegal28 microprocessor, ATmegal28 has 2 serial ports, and SPI interface, which can meet the above functional requirements. In addition, it also has rich I / O port resources, which can be used to drive sound and light alarms and relay actions. ATmegal28 has a built-in 4 KB EEPROM that can be erased and written 100,000 times. Because the home host needs to manage the location information and ID of the wireless anti-theft alarm probe, store the alarm phone of the alarm user, the content of the alarm message, the number of alarms, etc., 4 KB of EEPROM can solve this problem well. When the microprocessor receives the alarm information from the wireless transceiver module, it needs to analyze the data, find the list of activated wireless sensors, find the sensor corresponding to the ID number, read out its specific location information, and insert the location information into the After the preset alarm short message, it will be sent to the alarm user through the GSM module according to the alarm user list.
(4) GSM module The GSM network has high communication quality, good confidentiality, large network capacity, strong anti-interference ability, can realize global automatic roaming, and provides users with a variety of services such as voice, data, and short messages. A mature, most complete, widest coverage, and most widely used mobile communication system. The short message of GSM network transmits information through signaling channel, which is unique to GSM communication network. It does not need to dial to establish a connection, and can directly send the information to be sent to the short message service center SMSC plus the destination, and then the SMSC forwards it to the final destination at the appropriate time. The short message service, like voice transmission and fax, is the main telecommunication service provided by the GSM digital cellular mobile communication network. It is transmitted through the wireless control channel, and the storage and forwarding functions are completed through the short message service center. Each short message can send 70 Chinese characters, which can contain the name of the alarm user, the specific address of the alarm location, and the location of the wireless anti-theft alarm probe. Clearly describe the location of the accident site to ensure that security personnel can arrive at the accident site as soon as possible.
(5) Keyboard and display The keyboard can be used to set various functions of the home alarm, and the various states of the home alarm host can be seen through the display. Basic configuration operations can be set through the keyboard, some advanced settings need to be set through the configuration software installed on the computer. The basic configuration can make the alarm system work normally, and some users who are inconvenient to use the computer can also easily use this alarm system. The basic configuration operations include the switch of the home anti-theft alarm, the setting, activation and group management of the alarm user, the registration and activation of the wireless anti-theft alarm probe, and the management of simple alarm logs.
(6) Configuration software The home host is equipped with configuration software, which is installed in the home computer. The main functions of the configuration software are:
â‘ Alarm user settings. The name, mobile phone number and activation status of the alarm user can be set, and group management can be performed to distinguish the priority of different alarm users.
â‘¡Wireless anti-theft alarm probe settings. You can set the ID number of the wireless alarm, the position of the window where the wireless anti-theft alarm probe is placed, and the activation status.
â‘¢Alarm SMS settings. Set the preset content of the alarm message. When there is a wireless anti-theft alarm probe to send the alarm information, you only need to insert the name of the householder and the position information of the wireless anti-theft alarm probe into the preset alarm message, which can be sent directly to the GSM module.
â‘£Alarm log management. You can view the details of the latest alarm information and manage the alarm log information.
2.3 Design plan of the community host The community host is mainly used for user management in the residential community. The security scope covers the entire community. It is suitable for installation by the security department of the community and supervises the security protection of the entire community. 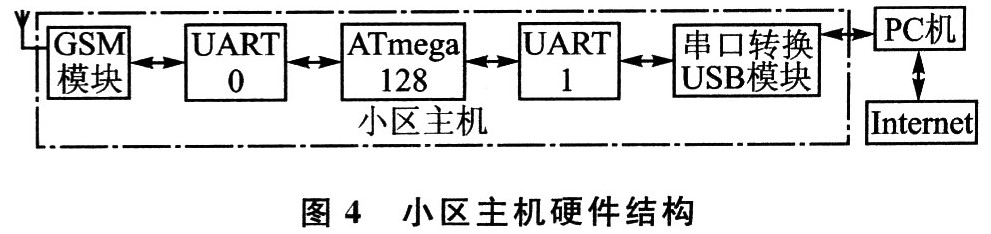
(1) The GSM module is the same as the home alarm host, and the cell host is equipped with the same GSM communication module. When the GSM module receives the alarm signal, it immediately transmits the alarm information to the microprocessor, and the microprocessor transmits the message information to the microprocessor through the serial port. PC software.
(2) Alarm function The main function of the software is to display the alarm information sent by the microprocessor in time and send out an audible and visual alarm at the same time to remind the staff on duty to react quickly and arrive at the scene as soon as possible.
(3) Data management There are many users in the host of the community, so you need to use a database for management. The host computer uses sQL server for user data management. The host computer software manages the users in the cell. When users in the cell use the alarm system for the first time, they need to send a registration message to the cell host or register personal information in the cell host by manual input to establish a database of cell alarm users. The upper computer software manages the alarm log and records every alarm in detail to facilitate searching afterwards.
2.4 Regional host design plan The management scope of the regional host involves the entire region, which may include several cells in the region. The users are larger, suitable for the installation of the local public security department, and can effectively assist in the management of regional security. The hardware structure of the regional host is the same as that of the community host, but the software of the host computer is more powerful, with a stronger database management function and map positioning system. Due to the gradual expansion of the management scope of regional hosts, the alarm methods may occur in parallel, so the most intuitive way to display them is to display their exact location directly on the map when an alarm occurs. Therefore, the regional host has good map data information, and can query geographic information data according to the address content of the alarm information, and directly display the geographic location corresponding to the alarm information on the map. If it can cooperate with the police force GPS positioning system, the police can reach the scene more quickly, and the loss of users can be minimized.
Conclusion This article expounds the design of the regional home anti-theft alarm system. On-site debugging proves that the alarm response of the wireless anti-theft alarm probe is timely and accurate, and its own sound and light alarm action can deter thieves. The home host can receive the alarm signal in time to drive a larger audible and visual alarm. At the same time, the home owner, other alarm users, community host and regional host can quickly receive the alarm message containing the precise alarm location, effectively guiding the security personnel in the community and region to arrive quickly The scene. This system can effectively prevent the intrusion of thieves, meet the security needs of users of different families, and can also assist the community and district management of public security, which has a very good application effect.
Introduction to the principle and design of regional home anti-theft alarm system of wireless network technology In recent years, with the improvement of living standards, the area of ​​family houses has been continuously expanded, the living environment is getting better and better, and the living quality of people has been significantly improved. At the same time, the rapid development of technology has driven the rapid development of electronic products, especially household electronic products have become an indispensable part of people's lives. The home anti-theft alarm system, which provides security protection for families and community users, has also approached people's homes.