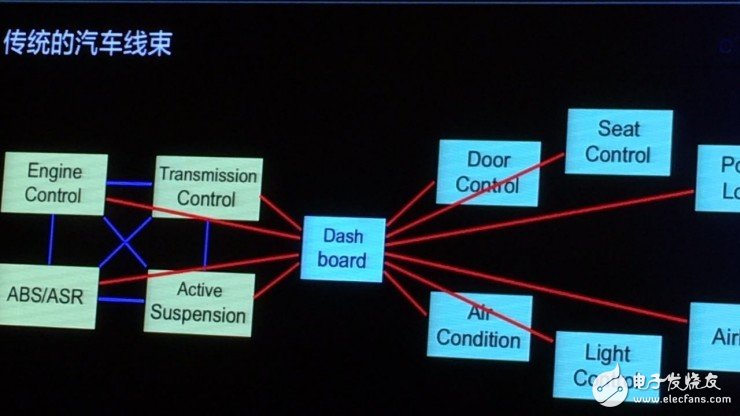
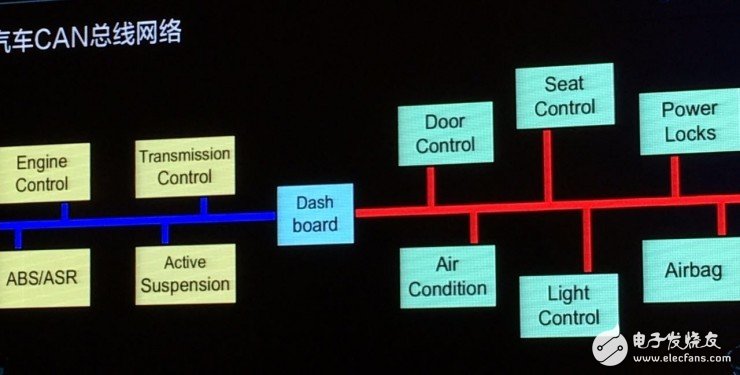
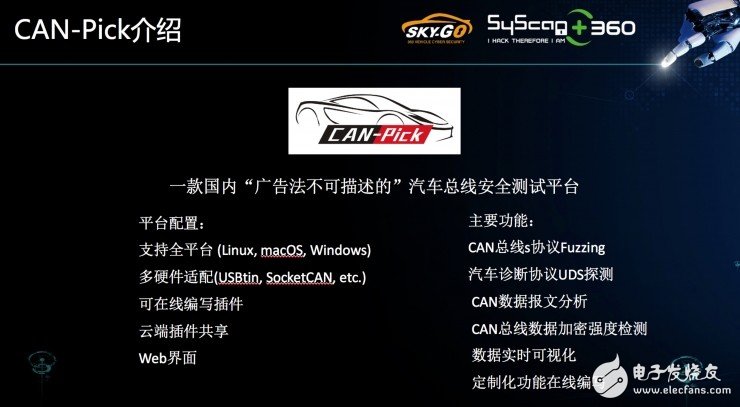
The first person to crack Tesla, the 360 ​​car network security center engineer Liu Jianwei also created a "universal car cracker": a new car bought by the eight children, can be easily driven away by him? ! In fact, in November, Liu Jianyi showed off this cool technology. In the 360 ​​company building, there were more than 20 luxury cars. Using mysterious technology, Liu Jianwei and the team easily solved the cars one by one. This time, he came to decipher in detail - how he did it. BUG left by CAN bus The source of all danger is the car's CAN bus design. CAN is the abbreviation of Controller Area Network. It was developed in 1986 by German BOSCH company, which is famous for developing and producing automotive electronics products, and eventually became an international standard (ISO 11898). It is the most widely used internationally. One of the widest fieldbuses. For cars, there are many ways to attack: OBD boxes, WI-FI, Bluetooth, car APP, car networking platforms... they are all controlled via the CAN bus. If the CAN bus is safe, even if the hacker uses the above-mentioned methods to make a move to the car, the overall safety of the car can be guaranteed. These tricks are just "entertainment". However, if the CAN bus is not safe, such a car can be attacked by a "dog strap" - it is useless to hold the car key, which is now a hacker who controls the CAN bus. How to guard the security of the CAN bus, from the structure of the CAN bus. The story started like this, a long time ago... The traditional car harness structure is like this: many controllers are linked on one thing, and the controllers may interfere with each other... Until one day, people can't stand it and design a bus architecture. Just like a switch, all ECUs (electronic control units) go through this "switch": exchange information and coordinate commands. However, it seems that the CAN bus has several deadly attack points: 1. It complies with the CSMA/CD communication method. When any node is connected to the bus, the bus data can be seen, so the hacker can find all the data in the car as long as he finds a point to break. 2. It supports multiple access. All nodes on the network receive data through a bus. All data is on one line. The data sent is broadcast, so you can see the control commands sent by many controllers. If the control command is Clear text, then you can control some of the car's equipment by replay; 3. It has a collision detection mechanism. All nodes continuously detect the transmitted data during the process of sending data, preventing conflicts with other nodes. Because of this mechanism, as long as the data is sent in the traditional line, it can lead to The CAN bus refused service and no controller on the car responded. Liu Jianwei introduced that as long as you know the data, ID, and transmission period of the CAN bus, the hacker can judge a certain control function through replay. Therefore, the attack on the CAN bus is actually very dangerous. It can eavesdrop on bus data, falsify protocols, and implement replay attacks and denial of service attacks. This means that if you do these actions, the car is in extreme danger. Can the universal car cracker really crack all the cars? Yes, as long as the car has a CAN bus design. First look at the theoretical analysis - the automotive CAN network reverse process is mainly divided into four steps: screening, positioning, cracking signals, verification and preservation. The first step: screening Using some USB-CAN tools on the market to connect to the car's CAN bus, CAN data packets broadcast on the CAN bus can be obtained, and reverse analysis can be performed from a large number of data packets to find the desired CAN data packet. Step 2: Locate the CAN_ID For the control of a certain function of the vehicle body, only one CAN ID data packet is needed. At this time, it is only necessary to simply replay to achieve the purpose of the attack, and some functions require a combination of multiple CAN ID data packets. Yes, there are some CAN ID packets with counters that must be added to the attack to bypass the pre-crash system. The third step: crack the signal There are 8 bytes in the CAN_ID packet. What each byte represents and the numbers on these bytes are not fixed. For example, the value on the speedometer is calculated according to the formula. If it is changed to the desired one. The value (that is, changing the speed in the movie to death) requires a formula to get the correct result. In the process of testing, it is necessary to trigger the car action, then determine the change of CAN_ID, and then find the corresponding value, so that the signal and the car action can be cracked. Step 4: Verify and save Combined with the above results, the FUZZ tool is made, and then more car loopholes are discovered. If it is necessary to repair, it is of course possible. In practice, we must continue to solve some difficulties. Liu Jianxi said: "We took some traditional USB tools and connected them to the car. We found that the screen is very fast. When analyzing the CAN protocol, we must look at the execution and the eyes will be spent." In order to analyze the data clearly, without tools, create one yourself. Therefore, Liu Jianwei and his team created a "CAN-Pick". This "CAN-Pick" is their "car safety bus test platform" - test whether the car bus is safe. In fact, it is also a universal car cracker. Although, its appearance does not look so cool, it is just a small black box and a software platform that can be connected to the car. So, how exactly will this car be blacked out? With the computer and the small black box connected to the body, the body will also generate some data when it is at rest. These data are called interference data, and the first step is to obtain the interference data. When the small black box is connected, visual interference data will appear on the software platform; then, the vehicle light is operated to obtain the data packet when the light is operated, and the interference data is compared, thereby discovering that the operating light can be actually released. Instruction packet. By replaying this newly acquired packet, the headlights can be operated. The other operations are the same. Yan Minrui, another engineer at the 360 ​​Vehicle Network Security Center, introduced: This software supports the whole platform, there are a variety of hardware to be tested, whether it is on the market, or developed by yourself, will provide SDK, let you try it yourself. At the same time, you can write some plug-ins online. These plug-ins can be shared to the server. You can also download some plug-ins written by others from the server to share them. Many people can operate this software at the same time. This means that “all people†can join the “black car†– oh no, it’s a platform to test whether the car is safe. Since the CAN bus can be attacked and this tool can also detect if a car is safe, is there any way to stop this from happening? Liu Jianwei said that the car bus design was originally used in a closed network environment, and did not consider security issues. For the design of the bus network structure and control commands, it is necessary to enhance the verification measures between the ECUs, including the use of time stamps and verification. The method prevents replay crack attacks, increases the cost of the control protocol being reversed, and controls the security of the connected components. Their current thinking is to securely encrypt the CAN bus, for example, whether some encryption algorithms can be inserted in the data packet. Liu Jianxi revealed that at present, the research team of Tsinghua University is also conducting research in this field.
WARNING!
Do not plug two or more meters together!
IMPORTANT
Don't plug in an appliance where the load
exceeds 16 Amp. Always ensure the plug of any appliance is fully
inserted into the meter outlet. If cleaning of the meter is required,
remove from mains power and wipe meter with a dry cloth.
KEYBOARD DEFINITION
1). SET: Set price with button UP.
2). MODE: Exchange display state.
3). UP: Set price combined with button SET.
GENERAL FEATURES
1).Display line power.
2).Display and memory accumulative total power quantity.
3).Display and memory total power charge of price.
THE DATA DISPLAY
Press MODE button the data displays as follows:
W →KWh →PRICE →COST/KWH
↑_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _↓
1). Plug in socket and power on, the meter will display real power.
2). Press MODE button once again and release, the meter will display accumulative KWh.
3). Press MODE button once again and release, the meter will display total power charge.
4). Press MODE button once again and release, the meter will display COST/KWH.
SETTING PRICE OF COST/KWH
1). Press SET button during display COST/KWH,the first digital COST/KWH flash, press UP button to set it.
2). Press SET button once again and release, the second digital COST/KWH flash, press UP button to set it.
3). Press SET button once again and release, the third COST/KWH flash, press UP button to set it.
4). Press SET button once again and release, the fourth COST/KWH flash, press UP button to set it.
5). Press SET button once again and release, the radix point COST/KWH flash, press UP button to set it.
DATA CLEAR
Press and hold MODE button for 5 seconds will clear KWH,PRICE and COST/KWH data.
Power Backlit, Backlit socket, power meter Backlit, energy meter Backlit, backlit adaptor, backlit plug socket NINGBO COWELL ELECTRONICS & TECHNOLOGY CO., LTD , https://www.cowellsocket.com