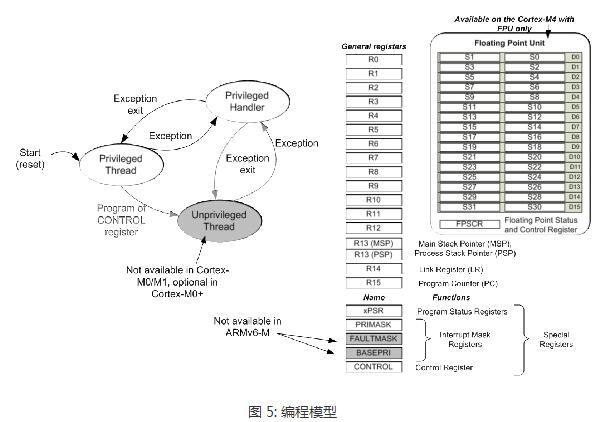
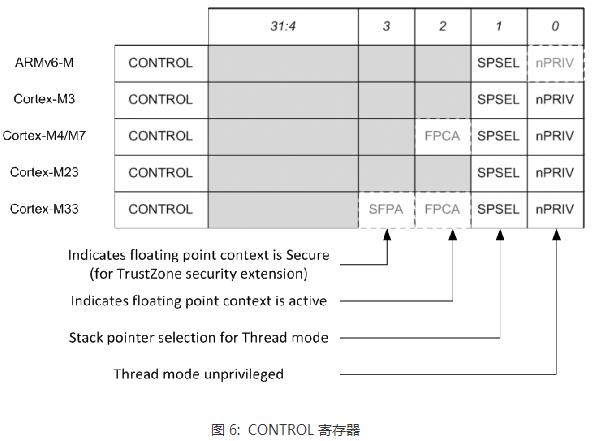
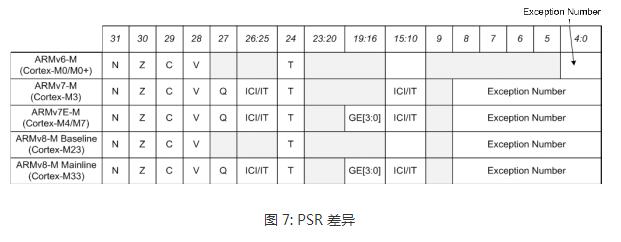
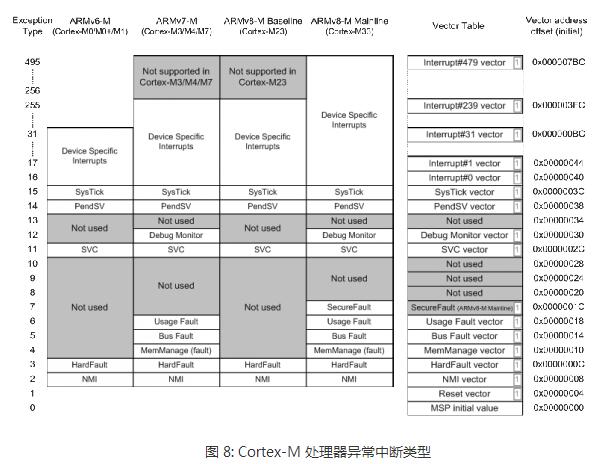
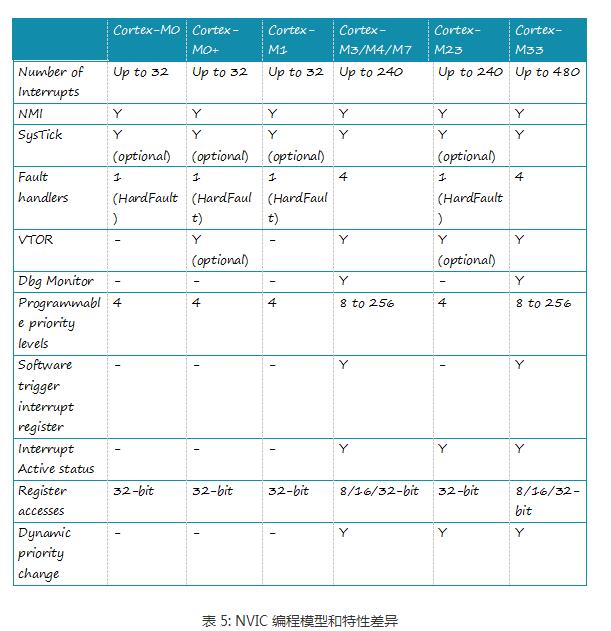
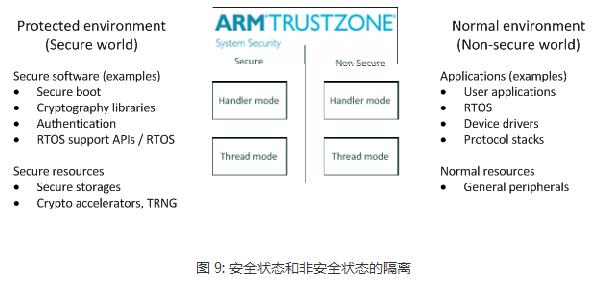
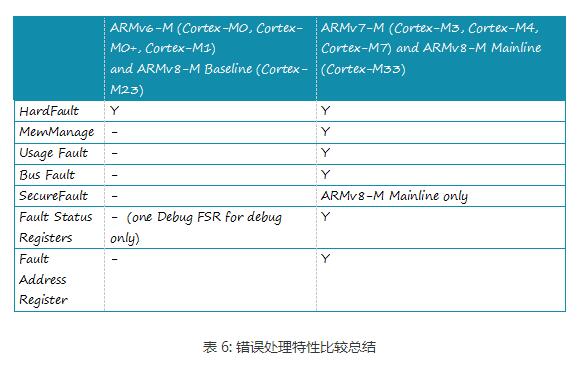
The Cortex-M is Atmel's new Atmel® SAM D20 microcontroller, which is based on a global microcontroller standard. Microcontroller processors are usually designed to have a small area and a high energy efficiency ratio. Usually these processors have very short pipelines and the maximum clock frequency is very low (although there are processors on the market that can run above 200 MHz). And, the new Cortex-M processor family is designed to be very easy to use. Therefore, the ARM microcontroller processor has been very successful and popular in the market of microcontrollers and deeply embedded systems. This article mainly introduces the architecture features of the Cortex-M processor, which are analyzed in detail from the programming model, exception handling model and nested vector interrupt controller NVIC, operating system support features, TrustZone security extensions, and error handling. Follow Xiao Bian together to find out. The programming model of the Cortex-M processor family is highly consistent. For example, all Crotex-M processors support R0 through R15, PSR, CONTROL, and PRIMASK. Two special registers - FAULTMASK and BASEPRI - supported only by Cortex-M3, Cortex-M4, Cortex-M7, and Cortex-M33; floating-point register set and FPSCR (Floating-Point Status and Control Register) register, Cortex-M4/M7 /M33 Optional floating-point unit. The BASEPRI register allows programs to block specified or low priority interrupts and exceptions. This is important for ARMv7-M because Cortex-M3, Cortex-M4, Cortex-M7, and Cortex-M33 have a large number of priority levels, while ARMv6-M and ARMv8-M Baseline have only a limited four priorities. grade. FAULTMASK is usually used for complex error handling (see section 3.4) Non-privilege level implementations are optional for ARMv6-M processors and are always supported on ARMv7-M and ARMv8-M processors. For the Cortex-M0+ processor, it is optional and Cortex-M0 and Cortex-M1 do not support this feature. This means that the CONTROL registers on various Cortex-M processors are slightly different. The FPU configuration also affects the CONTROL register, as shown in Figure 6. The difference between the other programming models is the details of the PSR register (program status register). For all Cortex-M processors, the PSR register is subdivided into the Application Status Register (APSR), the Program Status Register (EPSR), and the Interrupt Program Status Register (IPSR). ARMv6-M and ARMv8-M Baseline series processors do not support the QSR of the APSR and the ICI/IT bit of the EPSR. The ARMv7E-M series (Cortex-M4, Cortex-M7) and ARMv8-M Mainline (Cortex-M33 with DSP extensions) support the GE bit. In addition, the number range of the interrupt number of the ARMv6-M series processor IPSR is very small, as shown in Figure 7. Please note that the Cortex-M programming model and ARM7TDMI are not the same as these classic ARM processors. The definition of "mode" and "state" in the classic ARM processor is different from that in the Cortex-M except for the register set. Cortex-M only has two modes: Thread and Handler, and the Cortex-M processor always runs in Thumb state (ARM instruction is not supported) All Cortex-M processors include the NVIC module and use the same exception handling model. If an abortion occurs, its priority is higher than the current run level, and it is not masked by any interrupt mask register. The processor will respond to this interrupt/exception and push some registers onto the current stack. With this type of stacking mechanism, interrupt handlers can be written as a normal C function. Many small interrupt handlers can immediately respond directly to work without the extra stack processing overhead. The interrupts and system exceptions used by some ARMv7-M/ARMv8-M Mainline series processors are not supported by ARMv6-M/ARMv8-M Baseline products, as shown in Figure 8. For example, the number of interrupts for Cortex-M0, M0+, and M1 It is limited to 32 or less, there is no debug monitoring exception, and the error exception is also limited to HardFault (for details of error handling, see section 3.4). In contrast, Cortex-M23, Cortex-M3, Cortex-M4 and Cortex-M7 processors can support up to 240 peripheral interrupts. The Cortex-M33 supports up to 480 interrupts. Another difference is the number of priority levels that can be used: ARMv6-M Architecture - ARMv6-M supports two fixed (NMI and HardFault) and four programmable (represented by two bits per priority register) interrupt/abort priority. This is sufficient for most microcontroller applications. ARMv7-M architecture - ARMv7-M series processors have a programmable range of priority levels, which can be configured from 8 levels (3 bits) to 256 levels (8 bits) depending on the area. The ARMv7-M processor also has a function called interrupt priority grouping, which can further divide the interrupt priority register into group priorities and sub-priorities, which can specify preemptive priority behavior in detail. ARMv8-M Baseline – Like ARMv6-M, M23 also has a 2-bit priority level register. With the optional TrustZone security extension component, security software can shift the priority of interrupts in non-secure environments to the lower half of the priority range, which ensures that certain interruptions/abnormalities in the security environment are always less secure than non-security. The priority in the environment is higher. ARMv8-M Mainline - Similar to ARMv7-M. Eight to 256 interrupt priority levels and interrupt priority groups can be supported. Also supports the ARMv8-M Baseline priority adjustment feature. All Cortex-M processors rely on vector tables for exception handling. The vector table holds the starting address of the exception handler (as shown in Figure 8). The starting address of the vector table is determined by a vector table offset register (VTOR). 1. Cortex-M0+, Cortex-M3 and Cortex-M4 processors: by default the vector table is located in the starTIng of the memory map (address 0x0). Cortex-M0+, Cortex-M3 and Cortex-M4: The vector table defaults to the starting address of the memory space (address 0x0). 2. Cortex-M23 and Cortex-M23 and Cortex-M23 processors can have two separated vector tables for Secure and Non-secure excepTIons/interrupts. Cortex-M7, Cortex-M23 and Cortex-M33: The initial value of VTOR is defined by the chip designer. The Cortex-M23 and Cortex-M33 processors have two independent vector tables for safe and non-secure exceptions/interrupts. 3. Cortex-M0 and Cortex-M1 does not implement a programmable VTOR and vector table starTIng address is always 0x00000000. Cortex-M0 and Cortex-M1 do not implement a programmable VTOR. The vector table start address is always 0x00000000. The VTOR for Cortex-M0+ and Cortex-M23 processors is optional. If VTOR is implemented, the starting address of the vector table can be changed by setting VTOR. This function is useful for the following situations: 1. Relocate the vector table to SRAM to dynamically change the exception handler entry point 2. Relocate the vector table to SRAM for faster vector reads (if flash memory is slow) 3, relocation of the vector table to the ROM at different locations (or Flash), different program running phase can have different exception handler There are additional differences in the NVIC programming model between different Cortex-M processors. The differences are summarized in Table 5: In most cases, the operations of the NVIC's interrupt control features are handled through APIs provided by CMSIS-CORE. They are in the device driver library provided by the microcontroller manufacturer. For the Cortex-M3/M4/M7/M23/M33 processor, its priority can be changed even if the interrupt is enabled. The ARMv6-M processor does not support dynamic priority adjustment. When you need to change the interrupt priority level, you need to temporarily turn off the interrupt. The Cortex-M processor architecture is designed with operating system support in mind. The characteristics of the operating system are: Shadow stack pointer System Service Call (SVC) and Suspendable System Call (PenSV) exceptions SysTIck - 24-bit down timer that generates periodic abnormal interrupts for the timing and task management of the operating system Unprivileged Execution and Storage Protection Unit (MPU) Supported by Cortex-M0+/M3/M4/M7/M23/M33 A system service call (SVC) exception is triggered by an SVC instruction, which allows an application running in an unprivileged state to start a privileged operating system service. Suspending System Call Exceptions Scheduling non-critical operations such as context switching in the operating system is very helpful. In order to be able to place the Cortex-M1 in a small FPGA device, all features used to support the operating system are optional for the Cortex-M1. For the Cortex-M0, Cortex-M0+ and Cortex-M23 processors, the system clock SysTick is optional. In general, all Cortex-M processors support the operating system. Implementations on Cortex-M0+, Cortex-M3, Cortex-M4, Cortex-M7, Cortex-M23, and Cortex-M33 applications can run in unprivileged operating state and can use optional memory management units (MPUs) at the same time to avoid Invalid memory access. This can enhance the robustness of the system. In recent years, the Internet of Things (IoT) has become a hot topic for embedded system developers. IoT system products have become more complex and the pressure of time to market has also increased. Embedded system products need a better solution to ensure the security of the system, but at the same time it is easier for software developers to develop. The traditional solution is to divide the software into two parts: privileged and non-privileged. The privileged software uses MPU to prevent non-privileged applications from accessing critical system resources including security-sensitive information. This scheme is suitable for some IoT systems, but in some cases, only two layers are not enough. Especially for systems that contain many software components with complex privilege levels, a flaw in privileged code can lead hackers to completely control the system. The ARMv8-M architecture includes a security extension called TrustZone, which imports orthogonal partitions of both secure and non-secure states. Normal application is non-secure Software components and security-related resources (eg, secure storage, cryptographic accelerators, TRNG) are in a secure state. Non-secure software can only access non-secure storage space and peripheral devices. Security software can access all resources under both conditions. With this approach, software developers can use the past to develop applications in non-secure environments. At the same time, they can use the secure communication software library provided by the chip manufacturer to implement the secure IoT connection. And even if there are loopholes in privileged programs that run in non-secure environments, the TrustZone security mechanism can prevent hackers from controlling the entire device, limiting the impact of the attack, and enabling remote system recovery. In addition, the ARMv8-M architecture also introduces stack boundary checking and enhanced MPU design, facilitating the adoption of additional security measures. The security architecture definition also extends to the system level, and each interrupt can be set to security or non-security attributes. The interrupt exception handler also automatically saves and restores register data in the secure environment to prevent leakage of security information. Therefore, the TrustZone security extension allows the system to support real-time system requirements, provides a solid security foundation for IoT applications, and allows software development to develop applications on this technology. The TrustZone module is optional for the Cortex-M23 and Cortex-M33 processors. For more information on the ARMv8-M TrustZone, look for The Next Steps in the Evolution of Embedded Processors for the Smart Connected Era. For more TrustZone resources, see the TrustZone for ARMv8-M Community at community.arm.com. One difference between ARM processors and microcontrollers of other architectures is error handling. When the error is detected, an error exception handler is triggered to perform the appropriate processing. The triggering error may be: Undefined instructions (for example, Flash memory corruption) Access to illegal address space (for example, stack pointer crash) or illegal access by MPU Illegal operation (for example, when the processor is already trying to trigger an SVC exception in an interrupt with higher priority than SVC) The error handling mechanism enables the embedded system to respond to various problems faster. Otherwise, if the system crashes, the watchdog timing takes a very long time to restart the system. In the ARMv6-M architecture, all error events trigger the HardFault handler, and its priority is -1 (priority is higher than all programmable exceptions, but just below the non-maskable interrupt NMI). All error events are considered non-recoverable. Normally we only run an error report in the HardFault handler and further trigger automatic reset. The ARMv8-M Baseline architecture is similar to ARMv6-M with only one exception (HardFault). However, the HardFault priority of the ARMv8-M Baseline can be -1 or -3 when the TrustZone security extension is implemented. ARMv7-M and ARMv8-M Mainline products have several configurable error exceptions in addition to HardFault: 1, Memmanage (memory management error) 2, bus error (bus return error response) 3, usage errors (undefined instructions or other illegal operations) 4. SecureFault (supported only by ARMv8-M Mainline product, handling security and illegal operations in TrustZone security extension) The priority of these exceptions can be changed programmatically and can be turned on and off individually. If necessary, they can also use the FAULTMASK register to raise their priority to the same level as HardFault. The ARMv7-M and ARMv8-M Mainline products also have several error status registers that provide a clue as to the clues and error addresses that triggered the error exceptions to determine the access address that triggered the fault exception, making debugging easier. Additional error handlers in the ARMv7-M and ARMv8-M Mainline product sub-specifications provide flexible error handling capabilities, and error status registers make it easier to locate and debug error events. Debuggers in many commercial development kits already embed the use of error status registers to diagnose error events. In addition, error handlers can do some repair work at runtime.
Mobile phones and earphones have become necessities in our lives. How many people feel restless when they don`t have a mobile phone around. The mobile phone gives us a great sense of security to a certain extent, and its additional earphones also have such a function. . Wear headphones when you don`t want to talk; when you don`t want to listen to others, you wear headphones; when you don`t want to be harassed in an unfamiliar environment, you can play your favorite songs, be happy or sad, and enjoy your little universe most comfortable. There are now a variety of earphones on the market for people to choose from. From the original wired earphones to the current wireless Bluetooth earphones, they are more and more in line with people's requirements, and the sound quality and noise reduction are also constantly improving.
If you want to get a sports headset (sports scene) or a true wireless tws true wireless Bluetooth headset, what you expect from him is that it has the ability to withstand the test of different environments, wear it steadily, and have a long battery life, or it may be out of the street. Appearance, excellent sound quality, stable connection, friends who have certain requirements for sound quality and low requirements for noise reduction. You can take a look our earbuds.
Headphone 5.0 Handsfree,Cute Earphones,Mini Headphones,Ultra-Light Earbuds Shenzhen Focras Technology Co.,Ltd , https://www.focras.com